Are you at risk?
If you have an email address but no security to protect it, you are putting your business at risk – we explain why below, what it could mean to your business, and what you can do about it.
ICO Case Study
This ICO case study is a good example of what a successful phishing attack can mean to your business:
“What happened?
A law firm employee failed to recognise a phishing attack. They received an email, clicked a link to download a document, then inadvertently entered login credentials into what they believed was a legitimate website. A while later, the employee contacted the company’s IT department as they noticed they were no longer receiving emails.
Why was this a problem?
The data controller discovered the employee’s email account had been compromised when they entered their login details. A forwarding rule had also been set up, diverting the employee’s emails to a third party. Additionally, the third party had responded to several emails using a spoofed email account, advising the recipients of a change in bank details. This resulted in two clients making significant payments to the third party. The controller also discovered that the compromised email account contained scanned copies of client ID documents.”
You are responsible
GDPR requires you to ‘implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk’.
Impact
The impact to a business in the above ICO case study can’t be over-stated once you start factoring in the GDPR and ICO but a breach of this kind could result in :
- fines
- compensation
- reputational damage
Under Constant Attack
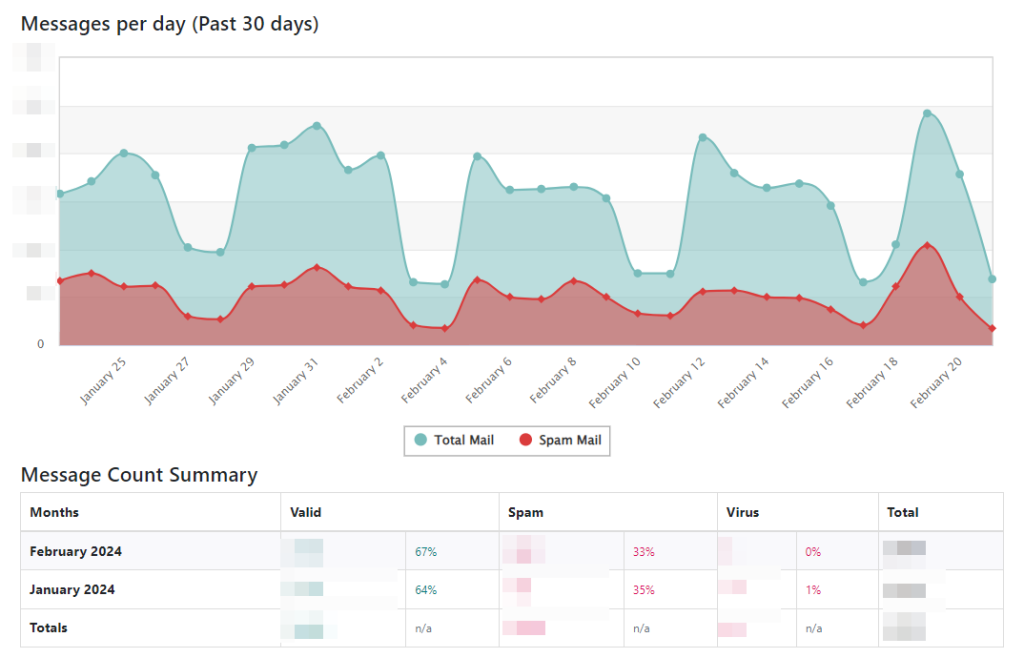
At the time of writing, our threat protection system currently blocks around 35% of our all our emails for Spam, phishing and malware. Of the blocked emails, 28% of these in the last 30 days have been phishing attacks.
Minimise your risk
Our threat protection system is multi-layered:
- link protection – every link received is replaced by a safe link; when clicked the system will live-verify the destination link to ensure it is safe
- impersonation protection – warn recipients or block emails which purport to come from a known user
- email and attachment quarantine – stop most threats before they get to you
- malware scanning – check attachments for malware
Protect Your Business Today
Further Reading
www.microsoft.com/en-us/servicesagreement
cloud.google.com/architecture/framework/security/shared-responsibility-shared-fate
ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/security/a-guide-to-data-security
ico.org.uk/for-organisations/report-a-breach/personal-data-breach/personal-data-breach-examples/


